

Power Mgmt.
Connectivity
Voice and Data, Messaging and IIoT/QKD Signalling Transport
Data Centre Monitoring PUE Power Utilisation Effectiveness
SUBPICO® RTC NETWORK
R E A L - T I M E - C O N T R O L
VPN | Onion alternative
TLS 1.3|Private End-to-End Encryption Protocol
Asymmetric Overlay Path
Real-time data source
On-Prem/Device Self-Management
"You cannot solve problems with the same thinking that created them." Albert Einstein
EXISTING CLOUDS FALL SHORT, SO WE BUILT OUR OWN.
IEC 60870-5-101/104/Ethernet Transport
Our protocol suite includes IEC 60870-5-101 and IEC 60870-5-104 connecting devices to each other and to other protocols.
Our service provides secure protocol translation data transfer between real-time field busses and centralised/distributed control centres.
Protecting the privacy, integrity, and confidentiality of vital operational services across energy, power systems automation, and other industrial sectors.
Power Management Solutions: Controlling Rack/Floor level ground to neutral line load.
Hard Real-time T/C bussing and load distribution









Connectivity for Real-Time Productivity, Commerce and Science
100+
2.5K+
POPs
CC
Interlace is a fully meshed global network that provides a controlled end to end path for point-to-point/multicast private and secure communications.
Transport Use-cases: IIoT/Industrial, Medical EMS Control/Signalling distribution, Cellular Slicing RAN/Core. Private Voice Data and Multimedia.
QKD (Quantum Key Distribution) - Interlace provides the ONLY viable solution to HNDL or SNDL (store-now-decrypt-later) Quantum Safe Computing. Having a photon stream based key to use over a point-to-point fibre link is fine but to have the key verified with the sender over a conventional channel defeats the purpose - state collapse if snooped. With a point-to-point fibre link (no active opto transceivers or muxs') the only way to 'sniff' the photon stream is with a passive splitter modifying the received power level while maintaining the signal integrity. Beam splitter and detection equipment can be applied.
Given the small range of fibre + limited commercial lambdas' it wouldn't be hard to field test fibre runs and build a control unit to adjust dynamically the passive tap/splitter power ratios.
Quantum keys dont secure or harden the systems using them or the wider network and services it relies on. With exposed micro-services the sharing and re-use of systems apps libraries factoring a prime is just a matter of time and the least of your worries.
Subpico networks start with securing the media first then the hardware processors/mcus' and controllers attached to that media, then the PCI hardware busses, system queues, memory (nmi/soft irqs) the drivers etc etc.
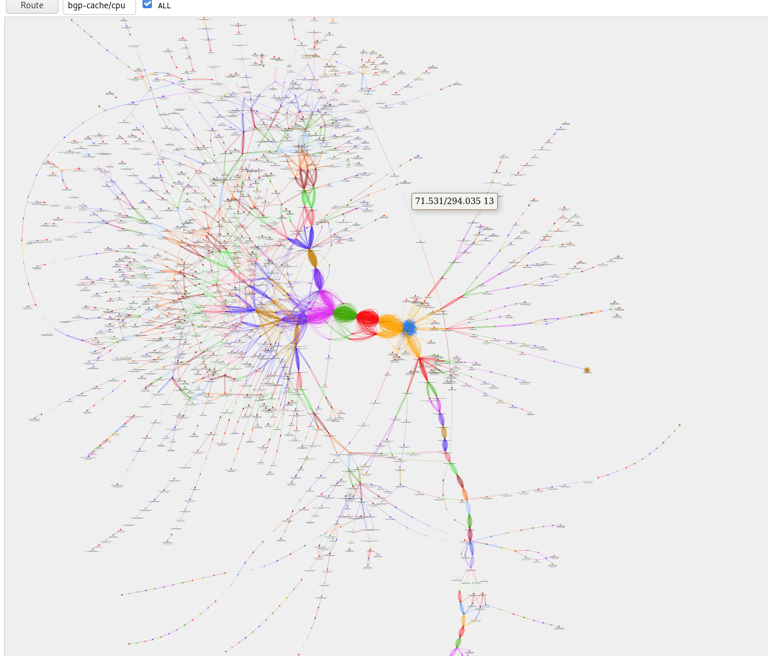
Fig B: Each of our nodes maintain a unique map of the Interlace network.
Fig B shows a map from the vantage point of the blue node at the centre of the picture.
The map is a live topology of where nodes are and the fastest paths to reach them.
Interlace Customers can apply global routing rules to avoid paths that transit certain regions and countries even cities.
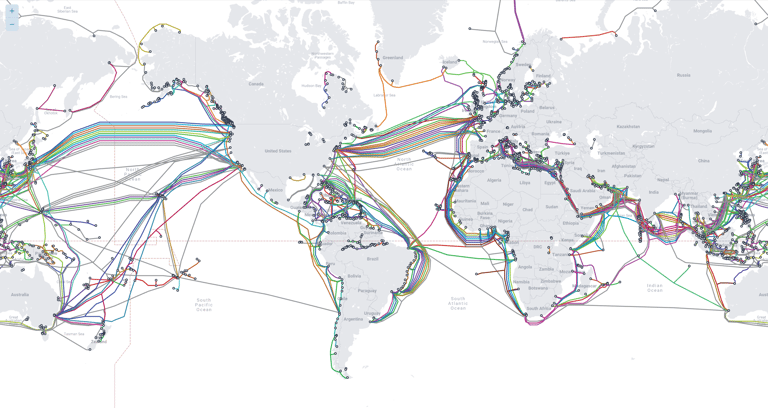
Fig D: Tier 1 landing points are selected in run-time by our nodes, policies and rules to reach the destination Tier 2 and 3/4 retail providers.
400+
Tier 3/4 CSPs
Subpico offers a practical and sustainable solution to reduce energy consumption without affecting productivity.
Subpico OEM MIB OID 1.3.6.1.4.1.45768
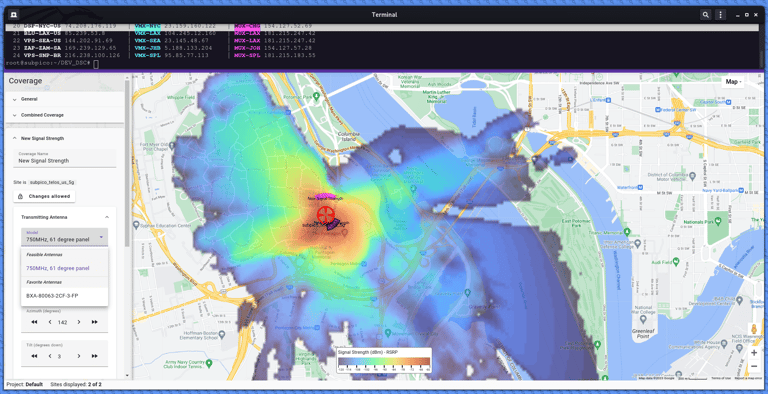
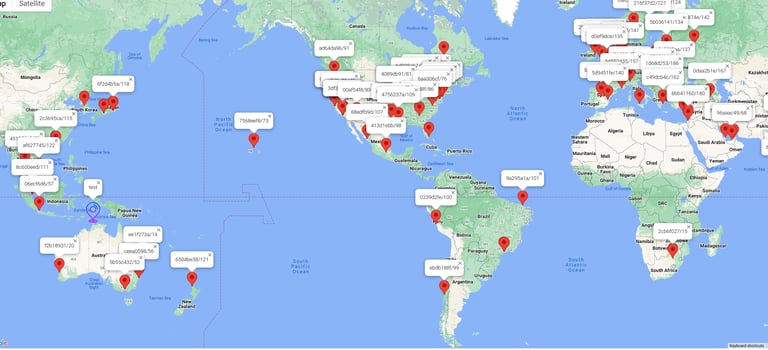


Fig A. Remote MVNO Radio Resource Control
Fig B. Node inter-carrier topology map
Fig D. Tier 1/2 Undersea Cable Landing Points
Fig C. Various Power Service Nodes
200+
T 1/2 GWs
V/CSP Private Interconnects + BGP/iBGP routing for an infinite degree of freedom on run-time fwd/rev path selection per packet.
Private and Secure Global Network
© 2025. All rights reserved.


