Applying Datasets to the OSI FSM to qualify SAPI time derivatives in a rotational frame of reference
First Order vs Higher Order Metrics with respect to and end point hardware device or application (inertial reference frame)
8/12/20255 min read
So what were trying to do is evaluate the time derivative of a vector in a rotating frame (remote network, device, application etc) and relate that remote moving time derivative to the equivalent time derivative in an inertial frame (local network/device/application etc) .
We want to do this because our understanding global/remote changes gives us preemptive actionable intelligence - for OEMs we can prepare memory traffic profiles and for our customers we can better protect and prepare, acting rather than reacting is always better.
There are many mathematical spaces but Cartesian's' are the most direct for our example.
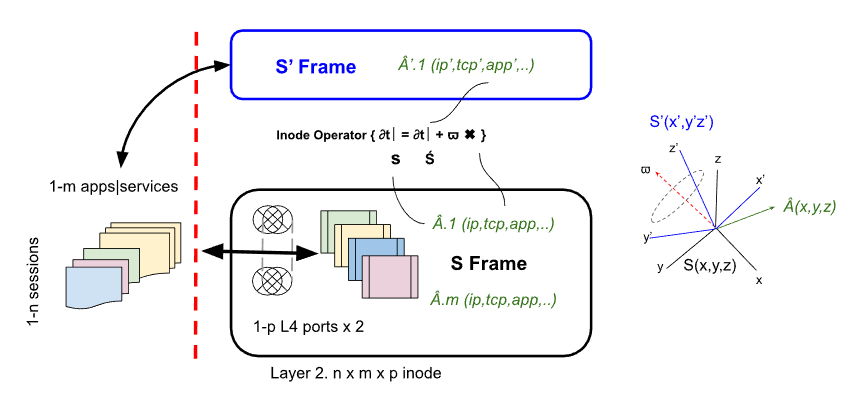
So basically we have 2 frames, frame S (our local thing we want to look after and adapt to any remote changes, it could be our customers systems, IoT device buss or networks) - in frame S we define a set of Cartesian coordinates axis - by convention labelled x, y and z. Frame S is inertial, so to us it's not moving or rotating i.e. axes are fixed in space.
Our second frame S' (remote systems probes/sensors) or S prime has a new system of Cartesian coordinates x', y' and z', and the new Cartesian coordinates are co rotating with frame S' in such a way that, if you were an observer sitting in S' the new co-ord x'y'z' system wouldn't appear to be rotating. Quantitatively frame S' is rotating with an angular velocity omega.
If we were to take a stationary particle sitting in S' (say a service flow IP:Port) at some arbitrary point and the angular velocity of S' is omega. From the perspective of someone in frame S (inertial or our local frame) the point is going anti-clockwise in a circle around the omega vector. The rate the particle or our thingy of interest (IP:Port) is moving around omega or rate of rotation is just the length of the omega vector.
Recall a vector has length or magnitude and direction, so in our case it tells us which direction and how quick the particle is spinning.
So lets start with some arbitrary vector in frame S, and what we do is take the time derivative of A as seen by an observer in frame S. What we're trying to do is form a link or understand how the time derivative in frame S maps onto the time derivative in S'.
To do this we have to expand the A vector into its components in the x' y' z' directions, and what we get is the time derivative according to someone in frame S against the A components in the S', => Ax' i' + Ay'j' + Az'k' where i,j,k are unit/basis vectors in S'.
So now with the product rule cause we have the sum of 3 products.
The derivation and expansion should be trivial for AI Data Scientists to follow.
What we end up with is a quantitative way to measure and analyse changes in remote qualitative phenomena, behaviour.
This is deeper than SQL/AI analysis or attribution from a sql query because its' 1) based on higher order derivatives and 2 puts the human investigator back in the loop.
Subpico Interlace provides the transport to deep-dive into changes in remote computing component, hardware and software. If your interested in changes in remote global systems - get in contact.
Interlace provides both quantitative and qualitative higher order metrics.
Higher Order metrics allow us to deep dive and understand the changes and impacts of connected resources, power, processing, and connections with respect to us, i.e. w.r.t us as an end-point or observer in an inertial frame.
When we measure remote app/service resources connection, state transitions, how does it change or compare with respect to some other end-points measurement, and how do we compare or relate these measurements against a group of say, field devices, CNC or servers, devices or applications, and how can we use this higher order data to our advantage. The communication access (local ISP) and transient networks (CSP's/VMNO's) etc give some good clues.
In simple and practice terms we are talking about heuristics or qualitative processing so we can preempt, protect and support our customers business and communications.
E.g. A qualitative understanding of busy-hour traffic across time-zones and countries lets us dimension our transport to support peak and plan for network loading and distributions in events like civil emergencies, concerts or football games etc. Or something as simple as high availability between HQ and satellite offices. Our working experience as telecom/network engineers is crucial.
All methods today in IT are quantitative and first order but some advances in AI like synthetic data is interesting.
The issue is its still based or rooted in first order data, and skewing it doesn't make it useful, in my opinion, finger printing a flow (been around since 2010's) which is just assigning a label or attribute to flow to check it against something someone decided was normal, the same goes with fingerprints. If there is a match, this doesn't say why or how because no TCPIP communication system is closed or reversible. To claim "we protect" or anything like that in cyber is to imply the system is both predictable and deterministic which requires an absolute degree of certainty is going to happen in the future and and happened in the past, i.e. there's no way to know for certain where or what in the protocol exchange caused the drop or session., e.g. TLS 1.3 PFS mandate, there are too many degrees of freedom in the upper layers of TCPIP to take fingerprinting and signatures. The answer is we need both qualitative and quantitative.
Basically quantitative tells you how high the tree is, qualitative describes the tree. But we need to know how high to describe the tree meaningfully.
Below is a mathematical approach we, Interlace, use as a global fabric to derive and understand global communication variations in stuff we (or our customers) are interested in. For us it's to build and test new technologies and innovations that is scientific measurable and repeatable.
Quantitative vs Qualitative Datasets
Traffic polices and Operation
Interlace opens all ports and disables all firewalls however in some countries there are a few public facing ports closed because of geo-political and regulatory restrictions.
While our inodes can sink DDoS in some countries and regions we need to terminate the remote connections to protect our underlying infrastructure providers.
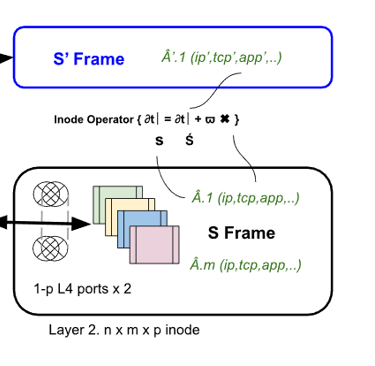
Pcaps - we can cut but its a little meaningless on the internet when it doesn't map to iana allocations. Our processing provides detailed sets including higher order ⇒ { ∂t∣s = ∂t∣Ś + ϖ ✖ } mappings e.g.syn/push, ecp etc time derivatives for connection analysis, content pdu vectors, malware binaries etc. That said we do record pcaps for new protocols and things of interest but only serve our learning heuristics.
our n-manifold design is a time derivative quantitative network vs mindless first-order qualitative net-flow, sFolw, IPFIX, pcap fingerprinting/signature logs designed for pretty dashboards. With the exception of LAN switch collapsed core logs and syslogs, we dont see the point if you cant control pps on a mirror/span port.
local CSP/Tier3/4 maintenance - With 400+ CSPs network maintenance and changes are an everyday activity. Interlace automatically checks and keeps SSL/TLS public keys (ECDSA key fingerprints) fresh to ensure customer delivery and operations are BAU (business as usual)
Our default traffic policy is to maintain sessions even if dormant to track flow clustering and bot activities etc
Harvesting Coverage
6 continents, 120+ countries, 400+ CSPs
2.5K inodes - covering All VM and container models, both dedicated and shared as well as in-situ colo appliances. Our inode microkernel can currently dissect and process over 30,000 protocols with ~ 150+ M active IP's flows per second per node.
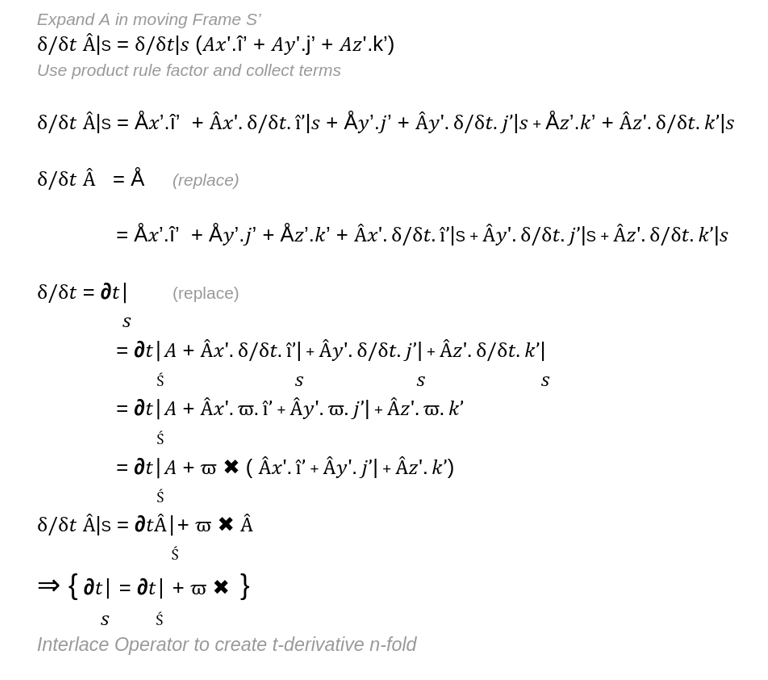
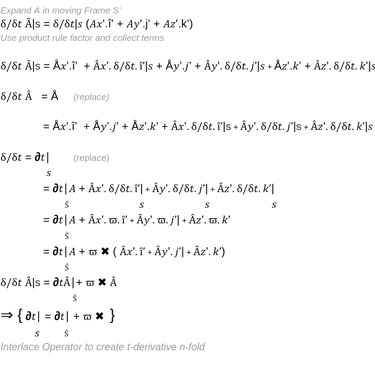
Interlace Higher Order Qualitative mappings
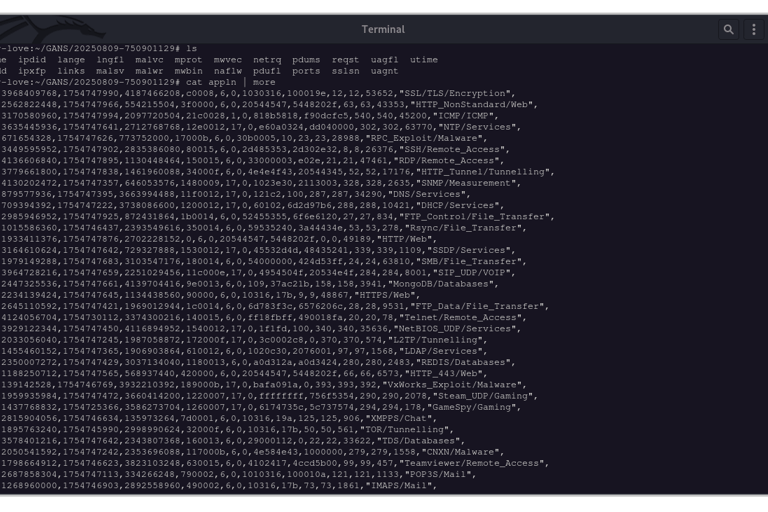
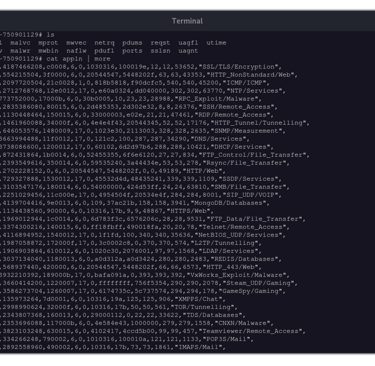
Dataset Type 2: Application CSV Quantitative - Interlace measures live 2nd/3rd order metrics against these variables to understand 1)initial conditions and 2) state changes.
Private and Secure Global Network
© 2025. All rights reserved.


